There are different types of cyber threat intelligence open-source tools . A large base of customization is applied. Let us explore more here. 1. Division of Homeland Security: Automated Indicator Sharing Privately owned businesses can report digital danger markers with the DHS, which are then appropriated using the Automated Indicator Sharing site. This data set lessens the viability of basic assaults by uncovering vindictive IP addresses, and email shippers, from there, the sky is the limit. 2. FBI: InfraGard Portal The FBI's InfraGard Portal gives data applicable to 16 areas of basic foundation. Private and public area associations can share data and security occasions, and the FBI additionally gives data on digital assaults and dangers that they are following. 3. @abuse.ch Abuse.ch is an exploration project facilitated at the Bern University of Applied Sciences (BFH) in Switzerland. This asset helps security groups track malware, botnets, IOCs, malignant URLs, and SSL declarati
Posts
A Guide To Understanding the Basics of Incident Response
- Get link
- Other Apps
Incident response is considered to be an organized approach that addresses as well as manages the aftermath of any security breach taking place against an organization. This cyberattack goes by the name IT incident, computer incident, or security incident. The goal of this organization will be to handle the situation in such a way that will limit the damage while reducing the recovery time and cost. What Is The Incident Response? The incident response activities are generally conducted by the organization's computer security incident response team. It is a group that is selected to include information security and general IT staff as well as C-suite level members. IR are steps that are used to prepare for, contain, detect as well as recover from a data breach. What Is A Cyber security Incident Response Plan? The incident response methodology includes a plan which is a document that outlines an organization's procedure, steps, and responsibilities towards the incident respon
Security Automation Platform: Everything You Need to Know is Here
- Get link
- Other Apps
With the abundant numbers of hackers lurking about the internet, it’s never been more imperative for websites to ensure that their company can defend itself against undesirable happenings. Cyber security automation helps to integrate and automate security analytics and operations activities more efficiently. Nowadays, there are so many hackers vying for top attention when uncovering errors and potential exploits in companies’ security systems. This rise in threats has led many organizations to seek strengthening methods to protect their digital assets better while eliminating burdensome points of vulnerability in their infrastructure. What is Cyber Security Automation? Cyber security automation refers to automated software that helps to identify and avoid cyber attacks and malicious events. Security analysts and experts use this concept as a threat intelligence to detect future vulnerabilities and respond to them quickly. Definitions of cyber security automation can be vague, so l
Security Orchestration Tools
- Get link
- Other Apps
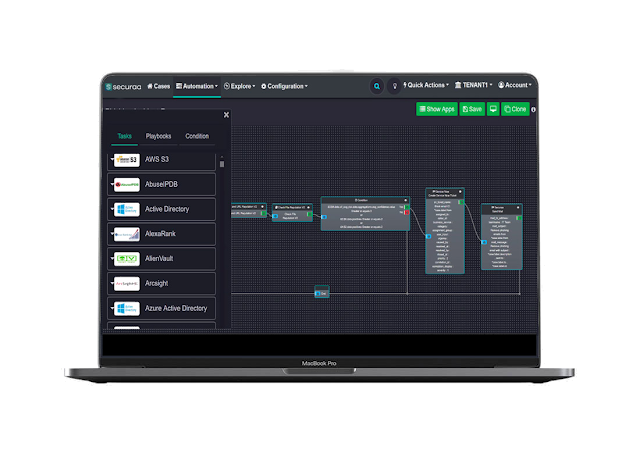
When it comes to keeping your business secure, there are a lot of things you can do. You could build your own security architecture, hire a team of security specialists to monitor your network, or you could outsource your security to a professional security service. One of the most effective ways to improve your security without spending a fortune is through the use of security orchestration tools . These tools are the secret behind many of the largest and most complex security infrastructures in the world.
soc automation
- Get link
- Other Apps
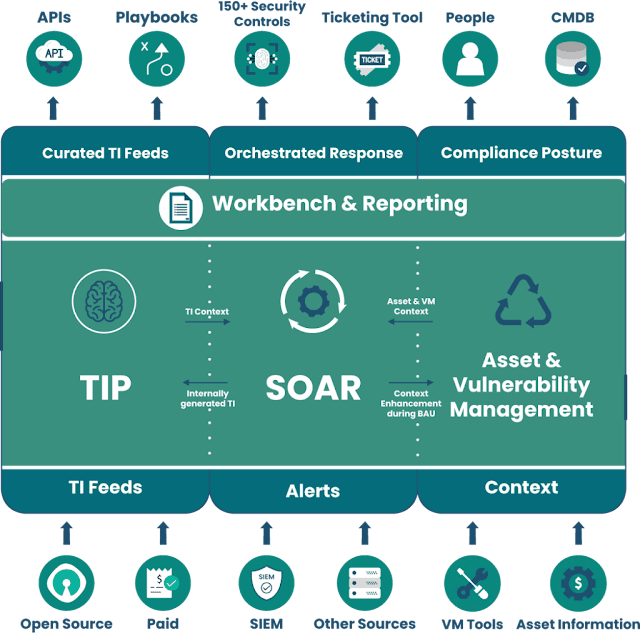
Besides manpower being indispensable, analysing hundreds of reported e-mails manually is an unnecessary task. This is where Security orchestration comes into play. It automates all malicious data into one place and based on this data, analysts can decide whether the data is malicious or not. https://www.securaa.io

